Compliance And Cybersecurity – Why Both Are Important

In the world of K-12 education, you’ll inevitably hear about the many ways to beef up your cybersecurity to ensure the safety of your staff and student data. However, another term is often heard when discussing cybersecurity: compliance. It’s not talked about as often, but both cybersecurity and compliance are essential for any school. Compliance […]
Why Gen Z Could Pose A Threat To Your Cybersecurity and How To Prepare

You may think that since they are the first full generation to grow up in the digital age Gen Zers are already well-prepared for any technological challenges and security issues that arise, but that isn’t always the case. Since most Gen Zers grew up with a smartphone and social media, they’re more likely to share […]
3 Cybersecurity Tips That’ll Save Your Bacon!

Be Careful Using Public WiFiWe’re all guilty of it: connecting to free public WiFi. Whether it’s at the coffee shop, hotel or airport, the temptation to check e-mail and surf the web is just too strong to resist. So BEFORE you connect to any free, public WiFi, make sure the connection is legitimate. It’s not […]
Keep Your School Compliant by Following These Technology Tips

A failure to remain compliant can spell doom. But what many Executive Directors and Operations Managers don’t realize is that compliance and security go hand in hand. Compliance is in place to prevent security breaches and give guidelines for what to do if a breach does occur. Your school won’t become compliant on its own. […]
Don’t Let Your School Become a Cybercrime Statistic

There are some records that you don’t want to be a part of setting, like this year’s expected record number of new data breaches. Keep cybercriminals out of your school and your pockets when you make smart cybersecurity choices. Answering the following questions can help you determine just how vulnerable you are. Are you… Using […]
Ransomware by the Numbers

Ransomware continues to be Public Enemy Number One in terms of IT security concerns, representing more than 60% of all malware attacks. As the threat of Ransomware grows, organizations are under increased pressure to protect themselves and their critical data. At IKON, we take data protection seriously and want to ensure organizations like yours are armed with […]
Devices Hacked by Linux Malware
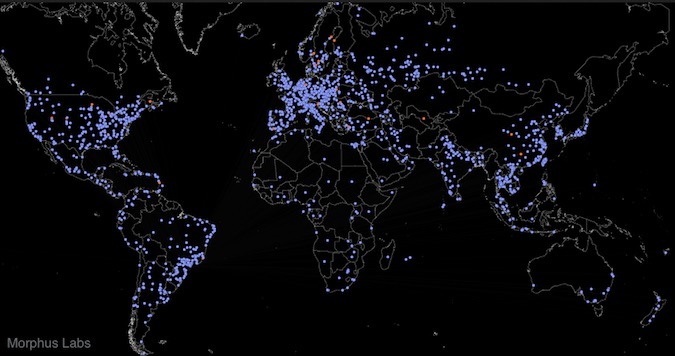
Thousands of devices have been hacked by a Linux malware named Rakos, and while researchers have yet to see any actual malicious activity involving the botnet, they believe it could be used for powerful distributed denial-of-service (DDoS) attacks. Rakos, whose existence was brought to light in December 2016 by ESET, targets Linux systems by launching […]
iOS Security Broken with a Simple Wi-Fi Connection

Apple CEO Tim Cook announces the new iPhone 7 during an event to announce new products, in San Francisco. The blurb for a presentation at the Black Hat Asia hacking conference this week would likely concern any iPhone owner: “The victim will only have to join the Wi-Fi network, and then the device will be […]
Linksys Routers Attacked by Hijackers Via Flaws

Attackers could exploit the vulnerabilities to crash routers, extract sensitive information from them or take them over The Linksys WRT3200ACM router. Two dozen Linksys router models are vulnerable to attacks that could extract sensitive information from their configurations, cause them to become unresponsive and even completely take them over. The vulnerabilities were discovered by senior […]
